The world's lightest, most secure service mesh, now with FIPS-validated cryptographic libraries
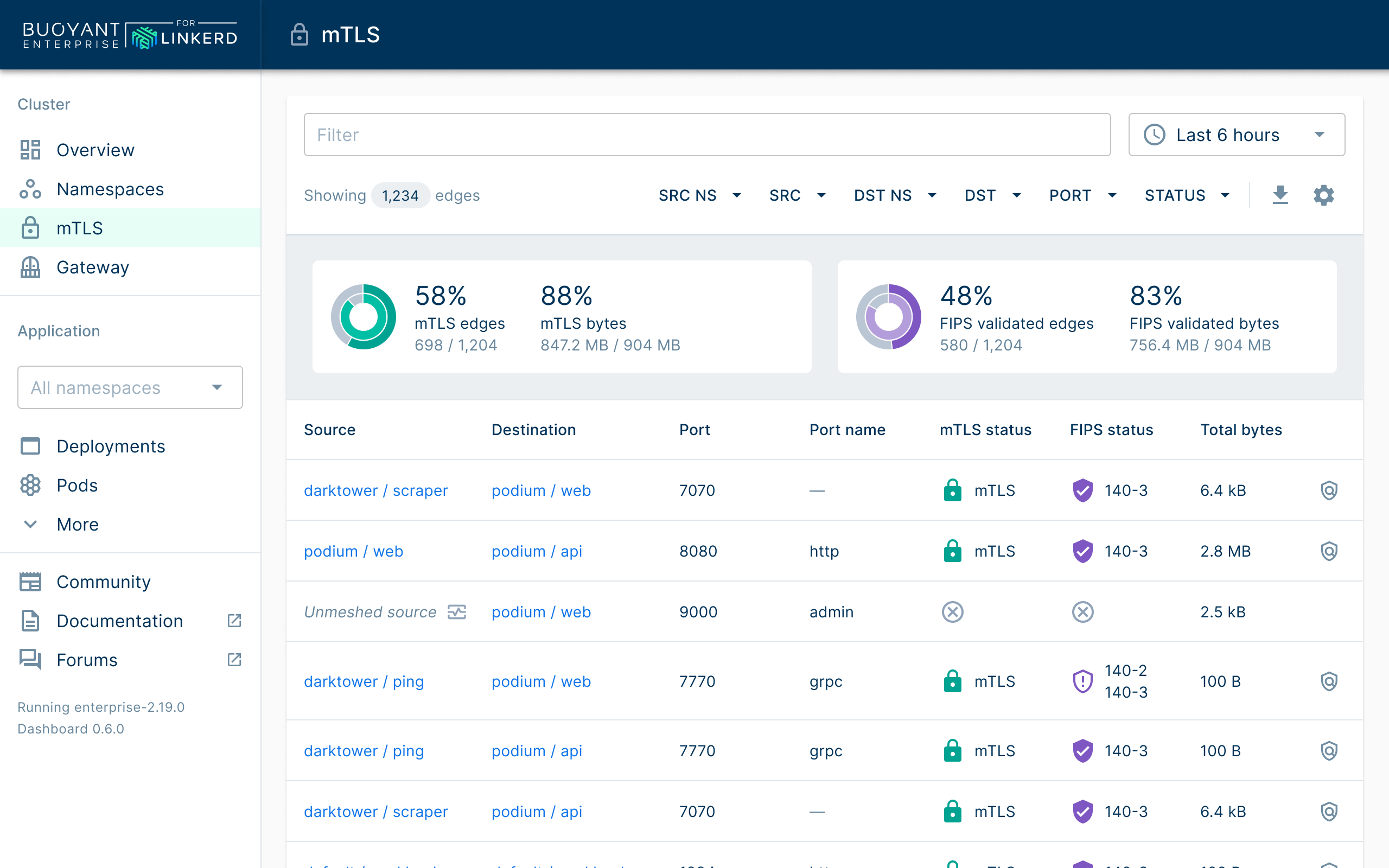
FIPS-validated encryption is a requirement for data at rest or in transit that is set by the National Institute of Standards and Technology (NIST). Buoyant Enterprise for Linkerd (BEL) uses FIPS-validated cryptographic libraries to transparently encrypt all data in transit between meshed pods.
FIPS-validated encryption is a key component to several compliance standards like:
For organizations targeting FIPS-validated encryption, Linkerd offloads the burden of individual application security to a centralized, validated infrastructure layer. Additionally, you'll get these key benefits:
Easy compliance auditing: BEL simplifies the auditing process with a FIPS dashboard to give auditors real-time proof of encryption as well as readily available CMVP numbers.
No code changes: Linkerd's FIPS-validated builds cover both Linkerd’s control plane and its data plane, allowing your application to have FIPS-validated encryption without changing its code.
Memory-safe architecture: Linkerd is the only service mesh that uses an ultra-secure "micro-proxy" written in the Rust programming language, avoiding critical memory safety issues that occur with other meshes (Istio, Cilium, etc.) that use Envoy proxies written in C++.
Industry standards security frameworks: Linkerd uses industry standards such as mutual TLS and Gateway API to provide a comprehensive suite of network security controls, including cryptographic workload identity, fine-grained micro-segmentation, deny-by-default, and true zero trust networking. With BEL, your service mesh is not only ultrafast, small, and simple—it's built for security from the ground up.
Integrated development and accountability: Unlike other service meshes, which have different projects for different parts of the tech stack, Buoyant builds both the control plane and the data plane with one team and one common goal. This allows Buoyant to provide a clear process for escalation, remediation, upgrades, and feature requests.

Buoyant's FIPS build of Linkerd is designed for organizations that must comply with NIST FIPS 140-2 and 140-3 standards and want a way to do that without having to change code. Many compliance frameworks require this level of encryption, including FedRAMP, HIPAA, and CMMC. While Linkerd is the lightest, most secure service mesh on the market, open source Linkerd uses cryptographic modules that, while well-regarded and considered highly secure, are not validated for FIPS.
We've helped companies like Zscaler build Kubernetes applications using FIPS-validated cryptographic libraries. If FIPS certification is a requirement for you, we'd love to chat!
We found Istio to be unnecessarily complicated. We would have spent months just learning the system, which isn’t an option when you’re in a high-growth stage like IntelliGRC. With Buoyant Enterprise for Linkerd, we could get it running immediately. Read the case study

Matthew DuVal
Head Engineer at IntelliGRC
Kubernetes-based SaaS applications need to be FedRAMP certified before they can sell to the federal government. Our ultralight Linkerd service mesh provides FIPS-validated encryption, authentication and authorization for all Kubernetes application traffic. Fast-track your FedRAMP journey and accelerate your time to market.